Cybersecurity: An Integral Approach

The impact related to the global problem of cyber-security can be put into perspective by using the four categories of objectives from the COSO-ERMii framework: strategic, reporting (including financial), operation and compliance. The organization’s overall strategy, including goals, initiatives in relation to new technologies, products and services, and investments, as well as client information, can be exposed, resulting in significant damage to a reputation that may have taken years to build. In 2012, the National Cyber Security Alliance (NCSA) presented a report whose key finding has been of concern (consciously or not) to thousands of organizations in regards to their reputation: 60% of small companies go out of business six months after a data breach.i
Availability is an important concept for any type of business. No matter whether it refers to the continuity of a data center, a customer service line, an online service or a mobile device, a business interruption is an event that should raise concern. The more the “Internet of Things” (IoT) concept evolves, the more dependent businesses (and individuals) become on network connectivity. It appears that at some point in time, the well-known “Maslow’s hierarchy of needs”iv pyramid will need to make room for internet connectivity. The California Medical Center, which spent more than a week without network and had to pay 40 Bitcoinsv to attackers in exchange for decryption of their data in February 2016, and Sony pictures, whose employees were locked out of the company’s computer network as part of an attack against the comedy “The Interview” in November 2014vi, are two significant cases of operations interrupted by cyber-attacks.
Cybersecurity is also a compliance concern. Several regulations, standards and their representing agencies require some level of protection from cyber threats. Agencies such as the Securities Exchange Commission (SEC)vii for public companies or the Federal Financial Institutions Examination Council (FFIEC)viii include specific cybersecurity requirements that should be met by some or all of their related organizations. On the other hand, regulations and standards may include HIPAA, FISMA, GLBA, PCI, HITRUST and others.
An Integral Approach to Cybersecurity
Regardless of the fact that reducing risk is not an easy task and that there is no risk-free environment, the right approach to cybersecurity will take the residual risk to a comfortable level. Whichever the approach, it should include a combination of efforts and techniques to cover the areas with greatest risks.
An integral approach arises from the following fact: vulnerabilities come from different sources and consequently, all those sources should be addressed in light of the risk assessment.
Part I: Risk Assessment
Going back to risk assessment basics, an integral approach starts with the identification of risks related to the achievement of the organization’s objectives. Considering that resources are limited and not every system component has the same contribution to the objectives, it is necessary to prioritize. Trying to cover all aspects of all systems can result in frustration.
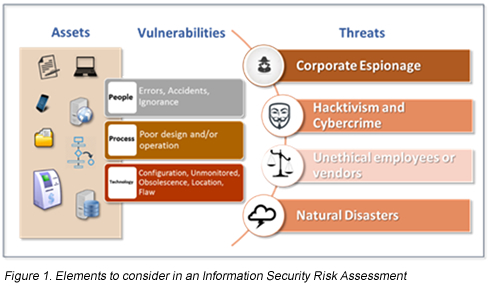
It is of fundamental importance to understand the relationship among the assets (both physical and logical), people, processes and technology, and their contributions to the objectives. Figure 1 presents an overview of the elements to consider in an information security risk assessment, which serves as the starting point to address specific cybersecurity risks. One of the “questions the board needs to ask” is: What are the top five risks the organization has related to cybersecurity?x
Part 2: Address Vulnerability Issues
Risks occur when threats exploit vulnerabilities. The following recommendations will help reduce the risk level by addressing the sources of vulnerabilities:
A. PEOPLE
Consider initiatives for three different audiences: top level executives (including board), Information Technology team, and the overall group of employees.
For top level executives, higher level training and risk assessment should be facilitated. To mention a few examples, articles such as “COSO in the cyber age”xi or “Cybersecurity: what the board of directors need to ask”xii have the language and proper level of detail to make them feel informed enough to ask questions and provide direction.
For the Information Technology team, a variety of technical and soft skills, as well as knowledge and experience are necessary (across different managerial and operational positions) to prevent, detect and counteract. Knowledge includes (but is not limited to) information security frameworks, security standards, security architecture, vendor specific certifications, security laws and regulations, and log management.
Finally, for all employees, awareness is imperative. Now, being in front of such a big concern, it is necessary to take this “awareness” to the next level, turning it into action. Time and dedication are required to obtain results from “the weakest link in the chain.” In his article “How to move employees from awareness to action,” J. Sherwoodxiii presents four levels of engagement. That process can be applied to motivate personnel to take action for cybersecurity: awareness (which stimulates the audience’s eyes and ears), understanding (which aims to reach the brain), commitment (which engages them, touching the heart) and action (moving employee to do something, to use their feet).
B. PROCESS
When considering processes, the integral approach goes one step further and integrates other enablers around the processes: policies, principles and frameworksxiv. Here are the key areas of action:
- Use the risk assessment as a starting point. This dynamic tool, as mentioned before, will help prioritize.
- Ensure that you have in place (and known by relevant personnel) policies and procedures. These should include activities for prevention (such as enforcement of a cybersecurity training class for key employees and an Intrusion Prevention System), detection (including a mandatory review of all access logs) and correction (e.g., a cyber recovery plan tested periodically).
- Consider the organization’s existing compliance requirements, to reduce overlapping efforts. If you already have to comply with HIPAA or PCI, as an example, map your cybersecurity-related activities to the initiatives required by those regulations or standards. You will probably save time and other resources.
- Finally, but most importantly, use available frameworks and standards to articulate processes, policies and principles; this will promote consistency, scalability and measurability. COBIT 5, NIST, OWASP and ISO 27001:2013 are good tools that include one or more areas for Information Security (IS) and can be used for cybersecurity.
C. TECHNOLOGY
Technology is the portion of cybersecurity that usually takes all the attention. In the integrated approach, it is just another key component of the overall solution. Technology encompasses the information management (from a technical perspective), infrastructure and applications. Although the policies and processes drive the use of technology, here are a few areas of action to consider:
- Identify and track all classified and Personal Identifiable Information (PII), and pay special attention at the configuration of the tools and devices that store, process and transfer and dispose of it. Different levels of encryption might be required at each stage of use.
- If third parties have access to classified information or PPI, such as an outsourced datacenter or hosted application provider, considering requesting independent reports of their control environment, such as a SOC 2.
- As part of the security risk assessment, vulnerability assessments and penetration testing should be performed periodically to determine the actual risk coverage.
- Ensure configuration management of devices and systems. This includes making sure that default passwords have been changed.
- If there is internal software development, promote secure development practices within a consistent methodology.
- Given the frequent use of credentials-related attacks, access management (including authorizations) should be constant.
- Using the layers of the Open Systems Interconnection (OSI) model, review the architecture components (from application through the physical layer) and ensure all higher risk assets have the appropriate level of protection.
- For hosts and devices that apply, ensure antivirus protection, with a regular update of virus signature definitions.
- Use monitoring systems that can alert in the event of a suspicious activity or deviation from an expected behavior.
In alignment with information security management, Cybersecurity is achieved through a combination of efforts and techniques; it is a process that involves different levels of personnel and skills. An integral approach will make sure that all relevant aspects of this challenge are addressed, including people, processes and technology. This approach, as any other, should be implemented and improved by using the well-known Deming cycle: planning the strategy according to the organization profile, doing all that applies to your risk profile in regards to the three aspects, checking the effectiveness of the initiative and acting when an opportunity for improvement has been identified.
ii COSO. (2004). ERM. Retrieved from Committee of Sponsoring Organizations of the Treadway Commission: http://www.coso.org/-erm.htm
i Strohmeyer, R.; PCWorld, 2013 citing the National Cyber Security Alliance (NCSA). Retrieved from: http://www.pcworld.com/article/2046300/hackers-put-a-bulls-eye-on-small-business.html
iv Maslow, A. (2013). A Theory of Human Motivation (Paperback). Watchmaker Publishing.
v Ragan, S.; “Ransomware takes Hollywood hospital offline, $3.4 million demanded by attackers,” CSO Online, February 14, 2016. Retrieved from: http://www.csoonline.com/article/3033160/security/ransomwae-takes-hollywood-hospital-offline-36m-demanded-by-attackers.html
vi Grisham, L.; “Timeline: North Korea and the Sony Pictures Hack,” USA Today Network, January 5, 2015. Retrieved from: http://www.usatoday.com/story/news/nation-now/2014/12/18/sony-hack-timeline-interview-north-korea/20601645/
vii OCIE; “OCIE’s 2015 Cybersecurity Examination Initiative,” Risk Alert September 15, 2015. Available at: https://www.sec.gov/ocie/announcement/ocie-2015-cybersecurity-examination-initiative.pdf
viii FFIEC; “Information Security: IT Examination Handbook,” 2006
x The Institute of Internal Auditors (IIA) et al; “Cybersecurity: what the board of directors needs to ask,” 2014.
xiii Sherwood, J.; “How to move employees from awareness to action,” 2014. Retrieved from: http://www.engagingleader.com
xiv ISACA; “Transforming Cybersecurity.” 2013.
\” Hackers Focus Shifts to Soft Targets”


















